⛳️ picoCTF2022: Local Authority
- 1 minLocal Authority
AUTHOR: LT ‘SYREAL’ JONES
Description
Can you get the flag? Go to this website and see what you can discover.
Point: 100
There is a login form on the website. Let’s see what’s in the source 🔍
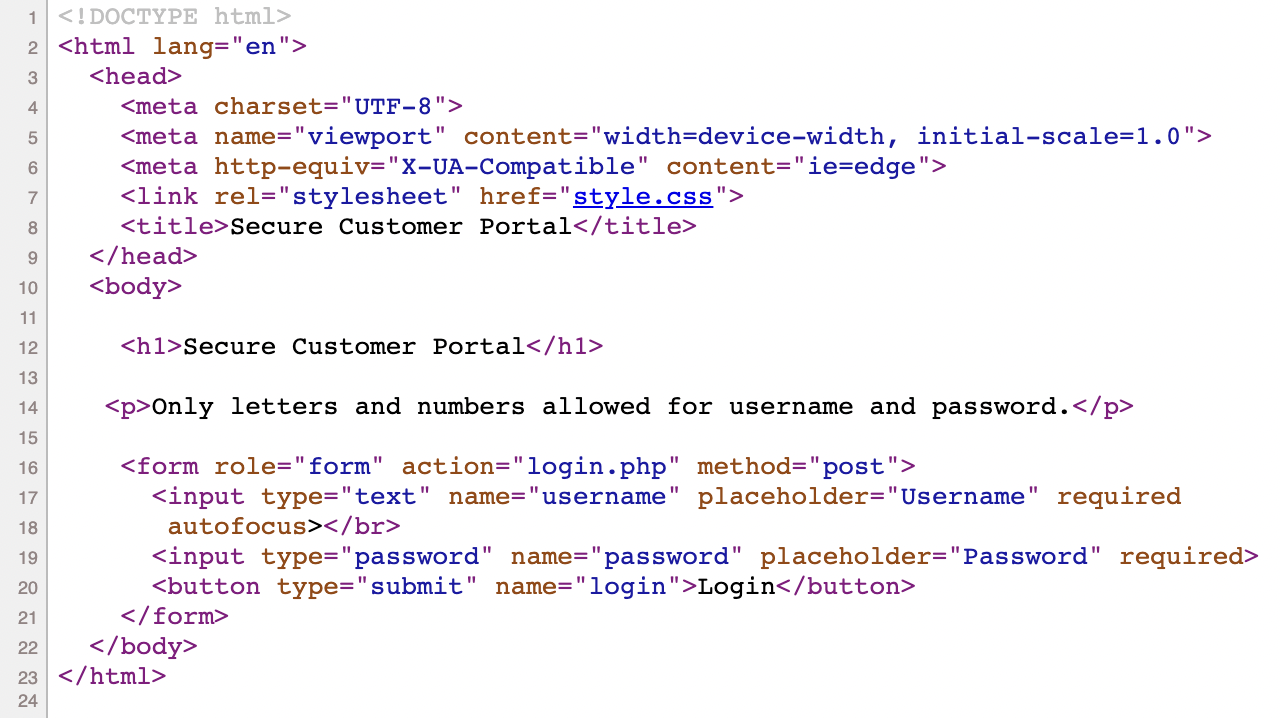
Nothing much on the page really. No .js file as well. The form is sending a POST request to /login.php Let’s try logging in!
You won’t be successfully log in, BUT you see what sources come with the request?
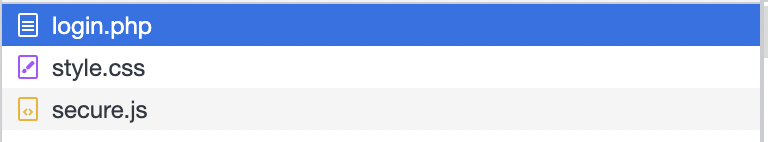
Double check with the login.php source, the secure.js and style.css are included. Let’s look at those files, shall we?
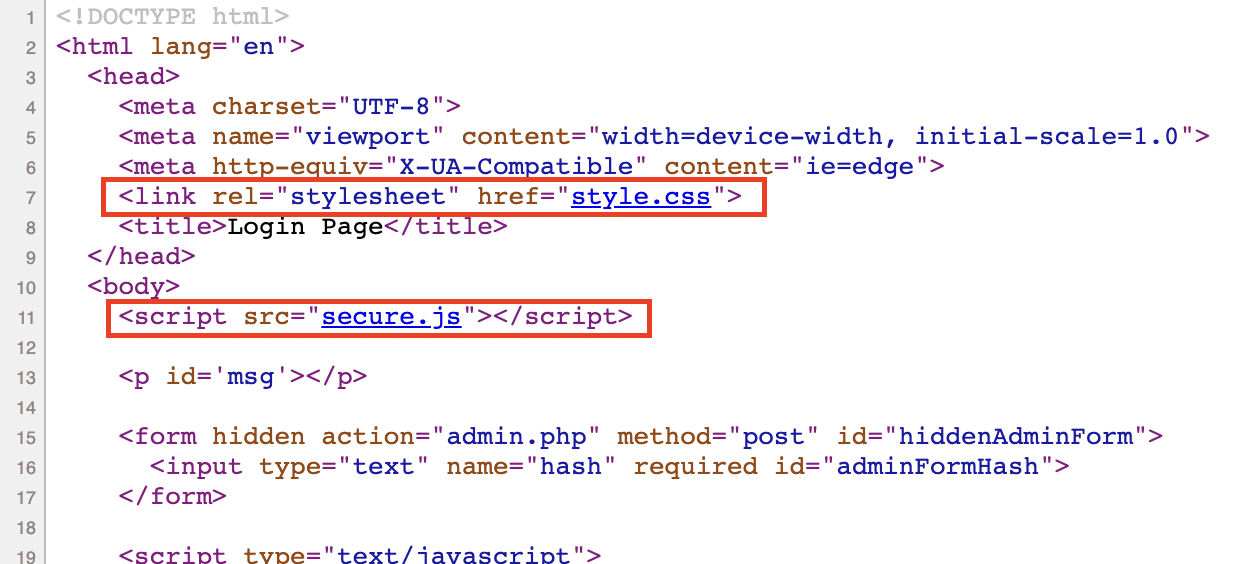
Nothing in css file. In secure.js, turns out, it’s not that secured at all. It’s hard-coded checking credentials.
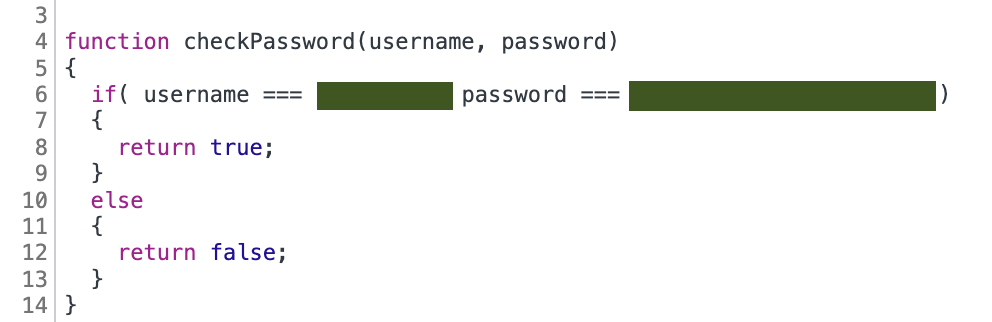
Once you get those credentials, go back and log in again. The flag shall be revealed 🚩
Closing Thoughts 💡
This is not a wise practice to authenticate the website on the client and hard-coded checking reveals credentials to the public. Typically, there would be a database to store users’ credentials. All passwords should be hashed (one-way function, not supposed to be reversible.) One popular algorithm used for this purpose is hashing with salt or so-called salted-hash. Salt is made of a unique random string added to an input of hashing function, which is a password in this case. It then results in a unique hash for each input even if inputs are the same.
If you want to go deeper on the salted hash, Auth0 has an article explaining the salted hash quite well.